
Stratis masternodes solve the problem of providing useful services to a blockchain network while keeping the list of services decentralised and tamper-proof. In the initial masternode implementation the service being provided is the Breeze Privacy Protocol, but it is anticipated that many more services can be added in future.
In order for this goal to be accomplished, each masternode must register (advertise) its existence via the Stratis blockchain. This is what is referred to as the Masternode Registration Protocol. A masternode registration simply consists of a specially formatted Stratis transaction. This transaction contains all the pertinent information needed by a client to connect to and validate the masternode.
A registration transaction, once submitted to the network, remains valid indefinitely until invalidated by one of the consensus rules governing such registrations. These are:
- The masternode server’s funding address is not funded within the initial window period.
- The collateral funds are insufficient at the conclusion of the window period (see section Collateral Verification for additional information regarding the collateral and the balance tracking).
- The collateral funds get moved, wholly or in part, to another address, thereby decreasing the balance below the required threshold.
- A subsequent registration is made at a greater block height than the original (e.g. to update the masternode’s public parameters).
- (Currently not enforced) A registration expires every N blocks, requiring the operator to periodically refresh it.
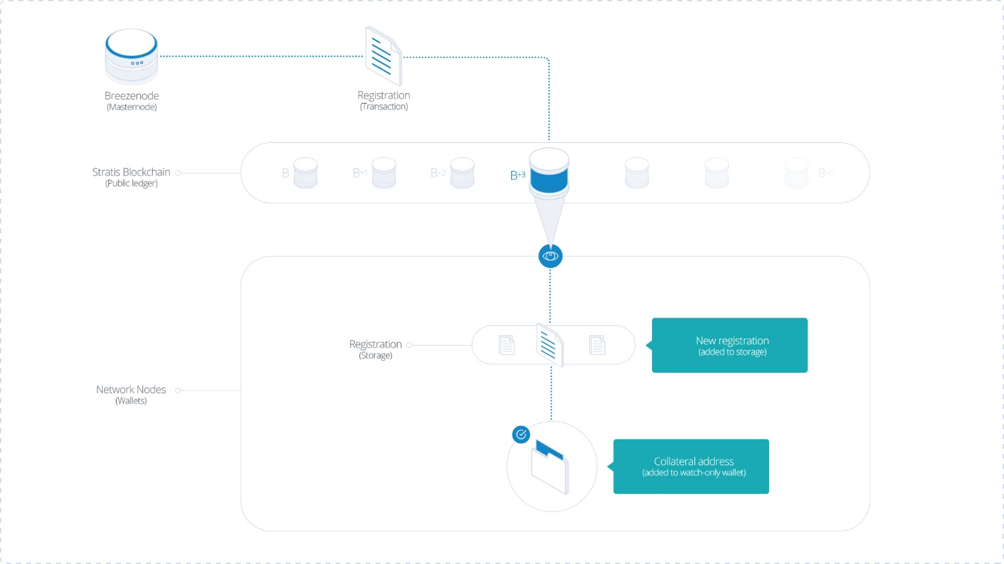
It is the responsibility of the Breeze client software to scan the Stratis blockchain for the most current masternode registrations prior to initiating contact with any server. They do this by observing each incoming block, looking for transactions that match the bitstream format. When a registration is found, it is stored in the node’s local store.
The block height that the registration is received at determines the window period for the masternode funding transaction. The masternode operator has to move the required collateral into the funding address before this window elapses. If this is not done the registration will be regarded as expired and purged from the local storage of all nodes on the network.
Once a sufficient number of valid masternode registrations have been downloaded, the client can select one at random and try to connect to it to utilise its services (e.g. the Breeze Privacy Protocol). Optionally the masternode selection can be performed once the entire blockchain is downloaded, as this is more fair to masternodes that register later in the chain.
The process described above has already been implemented into the Stratis software offering.
Bitstream format for masternode registration transaction
The registration transaction consists of a single transaction broadcast on the Stratis network (either testnet for testing or mainnet for ‘live’ masternodes). This transaction can have any number of funding inputs, as normal.
It has precisely one nulldata (data storage) output marking the entire transaction as a masternode registration. There can be an optional change return output, which if present must be at the end of the entire output list. The remainder of the transaction outputs are of near-dust value. Each output encodes 64 bytes of data into a public key script. The contents and format of the encoded data is described below.
The presumption is that the transaction outputs are not reordered by the broadcasting masternode, as this would result in potential data corruption.
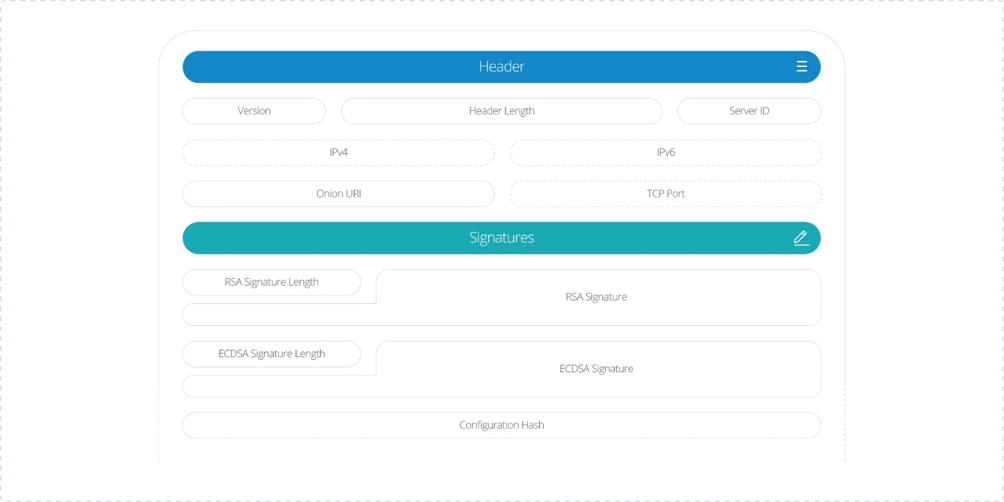
| OP_RETURN transaction output | ||
| Field | Size | Description |
| 1 | 26 bytes | Literal ASCII string: BREEZE_REGISTRATION_MARKER |
| Encoded public key transaction outputs | ||
| Field | Size | Description |
| 1 | 1 byte | Protocol version byte (if >200, it is a test registration to be ignored by mainnet wallets) |
| 2 | 2 bytes | Length of registration header |
| 3 | 34 bytes | Server ID of masternode (base58 representation of the collateral address, right padded with spaces if it is less than 34 characters long) |
| 4 | 4 bytes | IPv4 address of masternode, one byte per octet. Use 00000000 for an empty address. This field is not used for the Breeze Privacy Protocol; it is a placeholder for future functionality |
| 5 | 16 bytes | IPv6 address of masternode, one byte per octet. Use 00000000 00000000 00000000 00000000 for an empty address. This field is not used for the Breeze Privacy Protocol; it is a placeholder for future functionality |
| 6 | 16 bytes | Masternode server URI, currently this is an ASCII onion address hostname without any prefix or suffix. An empty address is signified by 00000000 00000000 00000000 00000000, but leaving this empty is not valid for the current Breeze Privacy Protocol implementation |
| 7 | 2 bytes | TCP port of masternode, may be ignored by client implementation |
| 8 | 2 bytes | RSA signature length in bytes |
| 9 | n bytes | RSA signature proving ownership of the Breeze Privacy Protocol server’s private key |
| 10 | 2 bytes | ECDSA signature length in bytes |
| 11 | n bytes | ECDSA signature made with the private key of the address used as the server ID. This same address is where the collateral will need to be located |
| 12 | 40 bytes | Hash of the Breeze Privacy Protocol server’s configuration file. This may be moved into the header in the next version of the protocol |
| … | … | The protocol format can be extended in future to accommodate new functionality. New fields should attempt as far as possible to retain backward compatibility with the existing fields |
On connection with the Breeze Privacy Protocol server by a client, the public key of the server will be verified by the client to ensure that the server is authentic and in possession of the registered keys. The Privacy Protocol is then followed as normal.
Collateral Verification
For the Breeze Privacy Protocol to function well, the creation of numerous or insufficiently powerful masternode servers must be disincentivised. Therefore, consensus rules that govern the validity of a masternode need to be established and enforced by participating client nodes.
A Stratis masternode requires 250 000 Stratis coins (STRAT) to be regarded as compliant. These coins should be kept in a single address, and should not be moved once the funding transaction is performed.
On receipt of each new block, the non-masternodes will check each transaction for those that affect a currently tracked masternode server. If funds have been moved out of the address, the calculated balance is decreased. If funds come in, the calculated balance increases. Once the balance has been computed for a masternode, its registration is automatically deleted if it falls below the 250 000 STRAT threshold. It is therefore not recommended that significant transactional activity be performed with the collateral funds, to avoid inadvertently invalidating registrations.
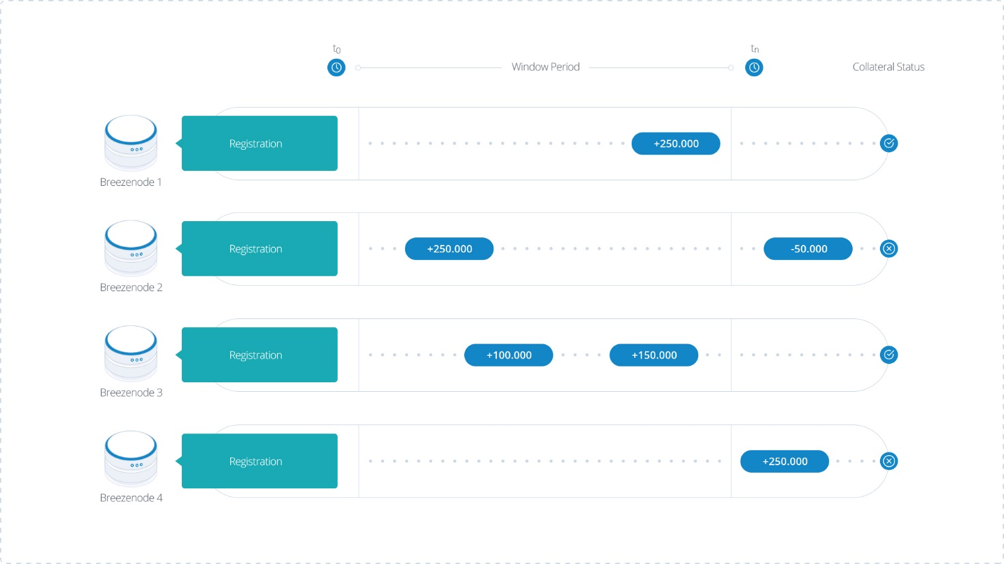
The above diagram illustrates 4 basic scenarios for a masternode’s registration sequence.
- Node 1 has made a sufficient funding transaction within the window period, and as such its collateral is regarded as compliant.
- Node 2 was initially compliant after the window period, but later removed some funds from the address, and therefore no longer has sufficient collateral.
- Node 3 made two transfers that when aggregated form sufficient collateral in the target address. This is a valid, but non-standard method of performing the funding.
- Node 4 took too long for the funding transaction to be performed (it was outside the window period), and is therefore regarded as non-compliant in terms of its collateral obligation.
The collateral verification functionality has also already been implemented into the Stratis software offering.
Future improvements
Inter-node discovery protocol
A drawback of the approach outlined in this paper is that every node has to download the entire blockchain from the genesis block onwards in order to accurately determine collateral balances. It is more efficient for registrations to be accumulated by full nodes, and circulated to their peers (full or light nodes) with sufficient proof of their accuracy.
The inter-node discovery protocol has already been implemented in the Stratis node software, but is not currently used in order to keep the initial version as simple as possible. It also has an indirect requirement for the peer policing described in the Peer policing model section.
Improvement proposal – peer policing model
There are some differences between existing masternode implementations and the envisioned Stratis masternode approach. Briefly:
- Dash masternodes are remunerated ‘passively’. This requires that they be actively pinged in a verifiable way by the remainder of the network to avoid paying a masternode that performs no work.
- Conversely, a Stratis masternode can currently only earn remuneration via active participation in the Breeze Privacy Protocol with connected clients. This removes the need to directly police the masternode in this sense.
- Due to the high cost of a top tier Stratis masternode, it is presumed that the operator will be economically incentivised to positively participate in the network. This is similar to the core tenets of the Proof Of Stake consensus mechanism.
There are also some aspects of the Dash approach that are desirable to emulate, particularly the ability to have the collateral in ‘cold’ storage.
The requirements for the Stratis top tier masternode may be summarised as follows:
- The node operator must be in possession of at least 250 000 Stratis (i.e. they possess the private key to move or spend them).
- These collateral Stratis must be present in a single address.
- Moving the Stratis collateral to a different address invalidates any proof of possession generated prior to the move.
These requirements need to be actively enforced to prevent dilution of the Privacy Protocol security model. It is proposed that the entities most suited to perform the enforcement are the masternode’s peers on the Stratis network. These peers may be one of the following:
- Another masternode (essentially a full node with additional features).
- A ‘full’ node with a complete copy of the Stratis blockchain.
- A ‘light’ node that does not retain a copy of the entire chain, but does at least retain block headers.
- Other types of nodes are outside of the scope of this document.
The onus is on a particular masternode to advertise its services to the network. This means that every node can elect whether or not to regard a masternode registration as valid, depending on the information it has available to it. From a game-theoretic perspective, it is advantageous for the operators of ‘rival’ masternodes to immediately present proofs of non-compliance of a particular masternode to the rest of the network. It is additionally presumed that there is no advantage to be gained for an honest node to propagate registrations known to be invalid.
An example of the ‘lifetime’ of a registration & implementation of the ‘proof of non-compliance’ concept is as follows:
- Operator configures masternode, which generates masternode registration Y on startup.
- Node operator moves sufficient collateral into address X (the ‘funding transaction’). This needs to be done within a finite window period after the registration transaction is made.
- Registration Y is broadcast as a transaction to peer nodes for inclusion into the Stratis blockchain in block Z.
- The registration is cached on each peer node. Nodes that join the network after block Z need not download the entire chain to receive registration Y – they can receive lists of verified historical registrations by communicating with their peers (inter-node discovery protocol). Light nodes can validate registrations for themselves by evaluating the Merkle proof of the registration against their locally downloaded block header storage.
- All full nodes on the network can directly evaluate the balance available in address X at any time. Therefore, if it transpires that a spurious masternode registration has been broadcast (which may happen) the full nodes will not forward that registration on to new peers. Peers that attempt to send known-invalid registrations will receive a proof of non-compliance in response.
- The status quo persists for a period of time without any changes that affect masternode registration validity.
- The masternode operator moves a portion of the funds from address X elsewhere, i.e. they are now below the collateral requirement.
- All nodes that download blocks will immediately be able to tell that the balance of X has changed, although a light node may not know what the actual balance is. Full nodes do know (or can calculate) what the balance is, and can construct a proof thereof showing that the masternode is no longer compliant.
- The non-compliance proof will be broadcast between nodes. This could be done pre-emptively (i.e. broadcast proof to all known peers immediately), or it could be done passively in response to receiving an invalid registration from a peer.
At a high level, the proof of insufficient funds will consist of the following elements:
- A copy of the ‘funding transaction’ for the masternode. This is defined in more detail in the Funding Transaction
- The registration record itself (in its entirety, as the peer may not have downloaded it yet).
- At least one complete transaction with the funding transaction included as one or more of its inputs i.e. showing that collateral funds have been moved/spent.
- The net result of the movement transactions must be that the balance of the collateral address is < 250 000 STRAT.
- Merkle proof(s) for the movement transaction(s) showing that they are included in a block at the same or higher height than the funding transaction.
A light node should be able to interrogate a peer node about the perceived status of one or more masternodes. If the peer being interrogated is also a light node, it will only be able to pass along proofs it already received and stored from the full nodes.
Funding transaction
The funding transaction for a masternode is the transaction that assigns the 250 000 Stratis collateral to a given address. It is recommended that only a single transaction output be used for this, to keep the size of the proofs communicated between peers to a minimum.
There is also naturally a possible gap between the block height of the funding transaction and the block height of the registration transaction, during which some fund movement may have occurred. This should not be a problem, as full nodes will evaluate the solvency of the masternode and determine whether to propagate its registration to other peers via the inter-node protocol.
Some possible attack/DoS vectors
The most vulnerable portion of the network are the light nodes. The proof mechanism therefore needs to be robust enough to allow the light nodes to participate in policing the masternode registrations without having the entire blockchain available.
The masternode operators also need to be protected from rogue full nodes attempting to stifle traffic to particular masternodes by censoring their registrations. This is mitigated by the decentralised nature of the Stratis blockchain. It is only required that a sufficient number of honest nodes participate to minimise or negate the impact of rogue nodes, as the registrations will percolate through the network via the blocks & inter-node protocol. A rogue full node cannot generate a fake proof of non-compliance, as the Merkle proofs will fail to be validated.
Masternode operators may generate copious registration transactions (i.e. spam) in an attempt to sway client nodes to use their server. This is mitigated by a rule that a client node will only keep the most recent valid registration for each known masternode, so spamming the network does not result in an increased likelihood that a client will select a particular masternode server.
It is important that a masternode operator avoid moving their collateral funds in such a way that they inadvertently provide an avenue for full nodes to construct a non-compliance proof. If funds need to be moved it is recommended that an entirely new address be used & a new registration performed. This will naturally cause the previous registration to be invalidated and removed from the caches of nodes on the network. The new registration will, conversely, be cached and used going forwards.







